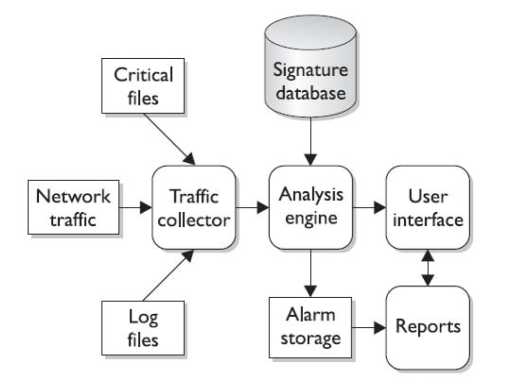
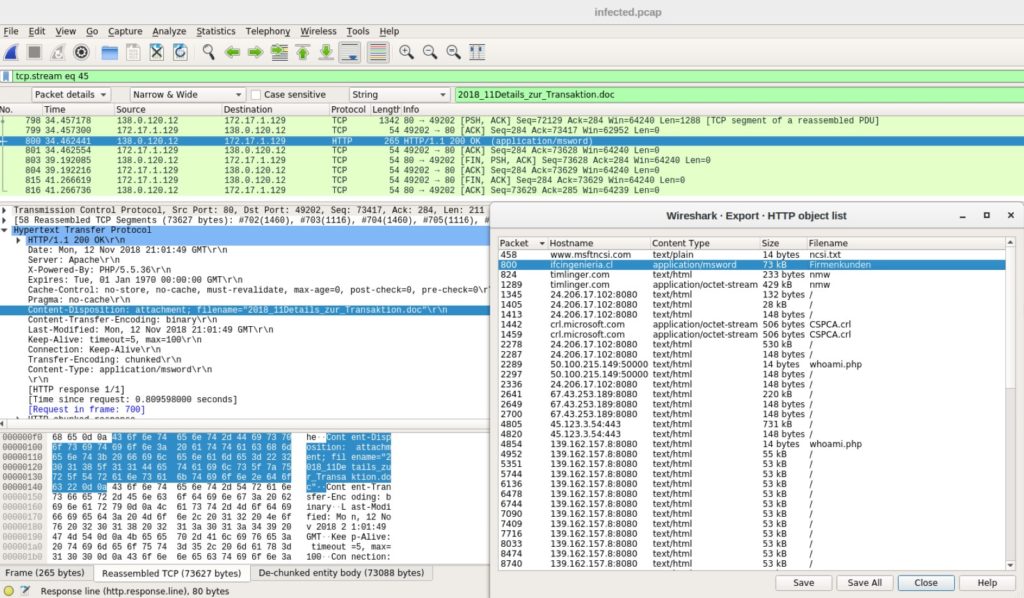
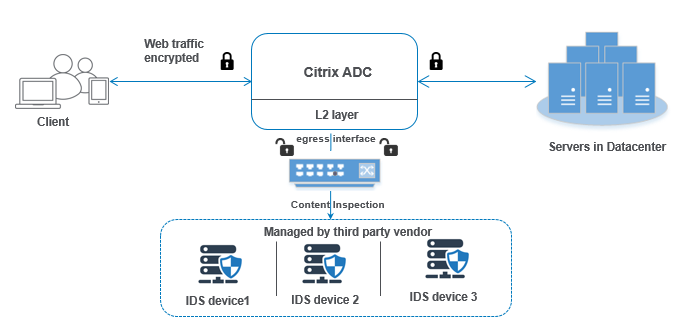
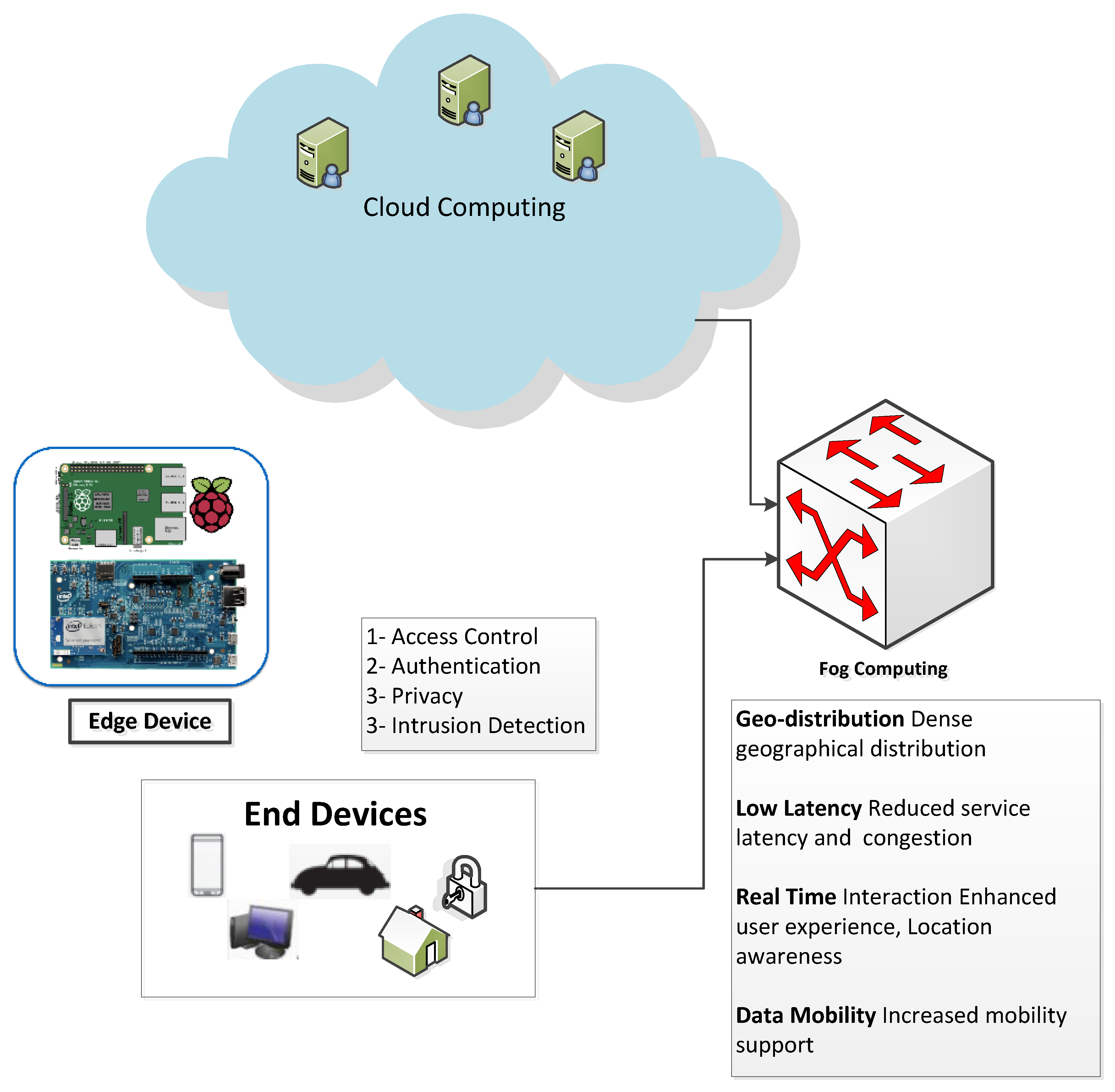
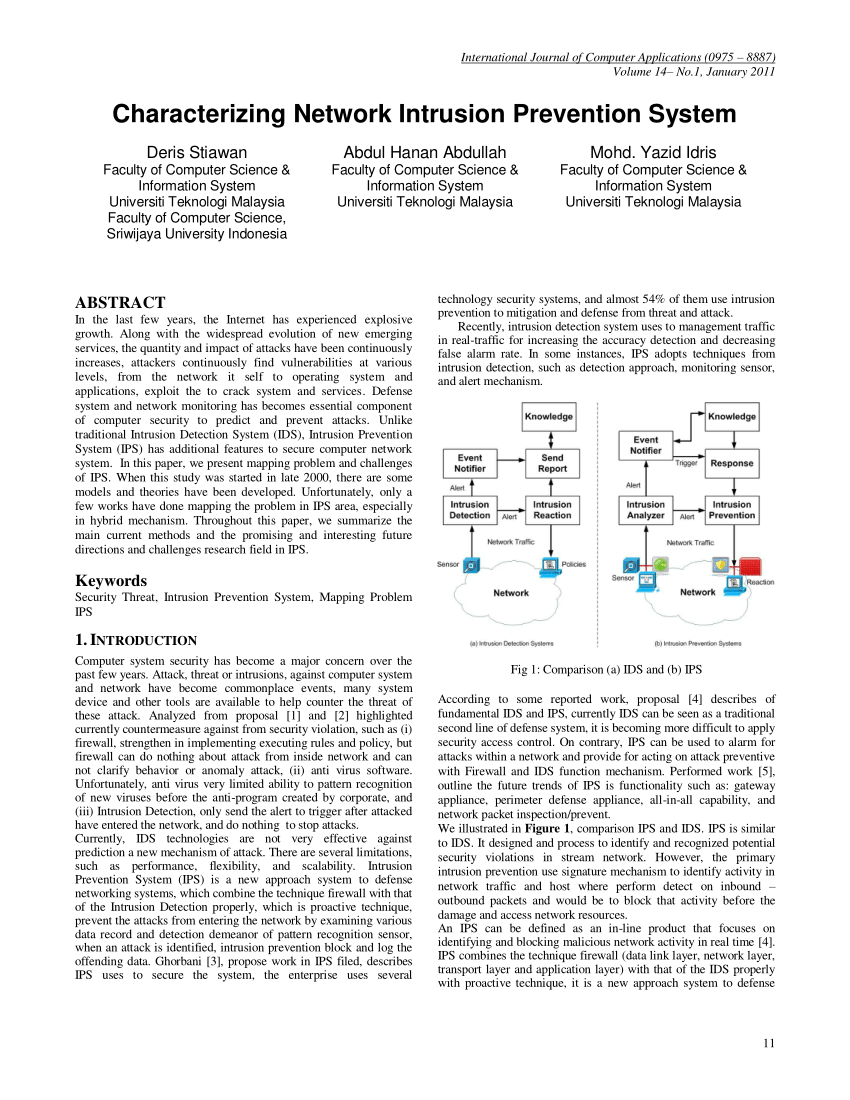
Any malicious venture or violation is normally reported either to an administrator or collected centrally using a security information and.
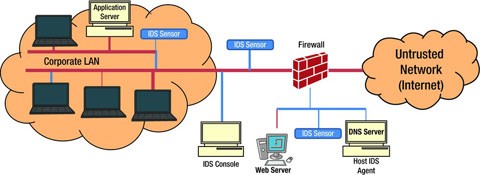
Intrusion detection system components include.
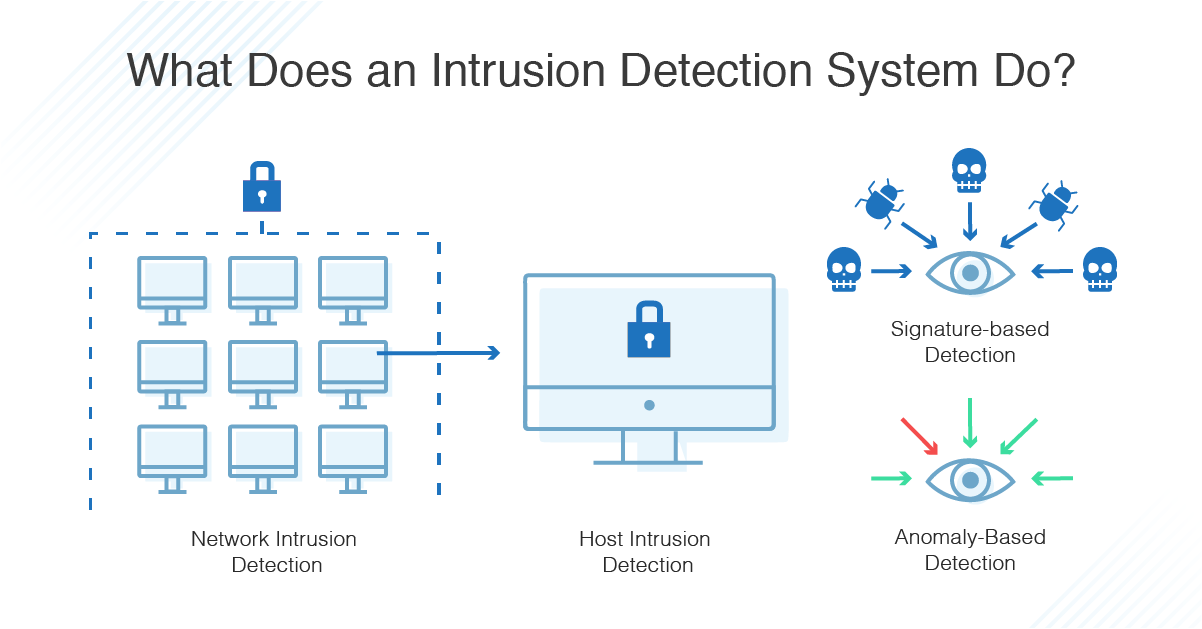
Host intrusion detection system.
The key is then to detect and possibly prevent activities that may compromise system security or a hacking attempt in progress including reconnaissance data collection phases that involve for example port scans.
It is a software application that scans a network or a system for harmful activity or policy breaching.
An intrusion detection system ids is a system that monitors network traffic for suspicious activity and issues alerts when such activity is discovered.
Find out what they do and how to implement them in your security stack.
An intrusion detection system ids is a specialized tool that attempts to determine when malicious activity is occurring within the network.
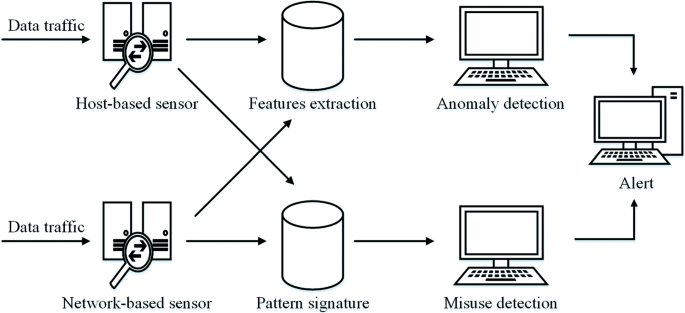
Some idses read and interpret the contents of log files from sensors placed on the network routers firewalls servers and other network devices and attempt to match.
Such a system works on individual systems where the network connection to the system i e.
An intrusion detection system ids is a device or software application that monitors a network or systems for malicious activity or policy violations.
Network intrusion detection system.
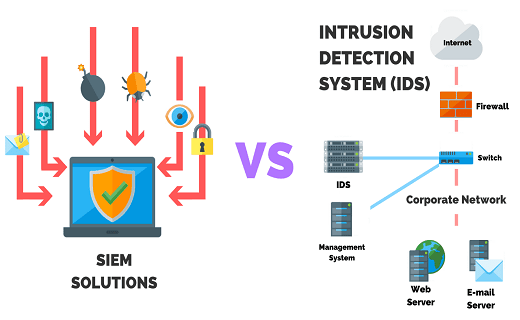
Intrusion detection systems ids and intrusion prevention systems ips are core components of a cybersecurity strategy but they don t act alone.
Intrusion detection system ids.
An intrusion detection system ids is a device or software application that alerts an administrator of a security breach policy violation or other compromise.
A full fledged security solution will also feature authorization and authentication access control measures as part of its defense against intrusion.
Intrusion detection system software is usually combined with components designed to protect information systems as part of a wider security solution.
Nids can be hardware or software based systems and depending on the manufacturer of the system can attach to various network mediums such as ethernet fddi and others.
Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management siem system.
Incoming and outgoing of packets are constantly monitored and also the auditing of system files is done and in case of any discrepancy the system administrator is alerted about the same this system monitors the operating system of the.
An intrusion detection system ids is a network security technology originally built for detecting vulnerability exploits against a target application or computer intrusion prevention systems ips extended ids solutions by adding the ability to block threats in addition to detecting them and has become the dominant deployment option for ids ips technologies.
A siem system combines outputs from multiple sources and uses alarm.